Researching Cybersecurity Challenges in Smart Home UX


Project Overview
Published Research: From Threats to Trust in Smart Home User Experiences
As part of my Computer Engineering thesis at the University of Wollongong Dubai (published in IEEE), I explored how cybersecurity threats impacted user trust and experience in Smart Home Energy Management Systems (HEMS). Using simulations and a genetic algorithm, I analyzed pricing attack vulnerabilities and designed detection and mitigation strategies to create a safer, more transparent, and user-friendly smart home experience.
Process Overview:
Project Overview
Published Research: From Threats to Trust in Smart Home User Experiences
As part of my Computer Engineering thesis at the University of Wollongong Dubai (published in IEEE), I explored how cybersecurity threats impacted user trust and experience in Smart Home Energy Management Systems (HEMS). Using simulations and a genetic algorithm, I analyzed pricing attack vulnerabilities and designed detection and mitigation strategies to create a safer, more transparent, and user-friendly smart home experience.
Project Type
Scientific Research
Tools Used
MATLAB (Simulations, Calculations & Data Visualization)
Microsoft Word (Report)
Duration
8 months
Team
Aksha Sajeev (Author & Researcher)
Dr. Haile Rajamani (Co-Author & Mentor)
Problem Definition
Cybersecurity Risks Undermining Trust in Smart Home Energy Systems
Smart Home Energy Management Systems (HEMS) have been proposed as a way of reducing energy consumption in households and for better utilization of electric grid resources.
In the race to become ‘sustainable cities’ and improve the cost and efficiency of energy consumption, more and more countries are slowly trying to shift towards this eco-friendly approach.

Problem Statement #1
Cyber-attacks on HEMS’ or multiple HEMS’ could lead to detrimental consequences on the smart electric grids as well as on smart homes.

Problem Statement #2
Repeated attacks will eventually give birth to distrust among users resulting in a decrease in the sales of the HEMS.

Problem Statement #3
After researching over 15 scientific papers, it was concluded that very less research had been done on possible types of attacks and vulnerabilities for HEMS’.
Why is there very little research on the attacks on HEMS?
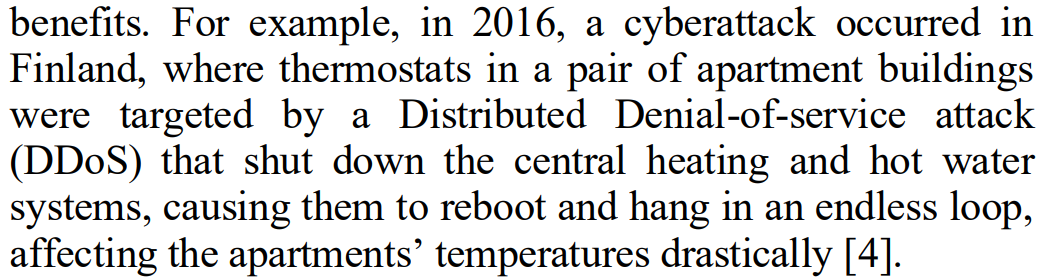
Cyber-attacks on HEMS is usually not considered because they are smaller systems that consume lesser energy. However, the below 2 examples prove that this problem cannot be ignored anymore, and must be thought about when setting up safety plans.
Solution
Objectives of this research
-
Investigate the cyber vulnerabilities in a HEMS operation within an ‘aggregator’ type market where an aggregator is involved with controlling the HEMS.
-
Simulate pricing cyber-attack on HEMS and evaluate both qualitatively and quantitatively the impact of this attack.
-
Develop suitable mitigating options.
Design Process
Understanding the HEMS architecture's vulnerabilities
To execute the objectives, the first step was to investigate all possible cyber vulnerabilities within the HEMS model. Research was also done to learn about different possible cyber-attacks that could take place.
This HEMS model also involved a solar panel within the system for supplying energy.
Grid operator
Communicates with the smart grid and provides the retailer with electricity prices.
Retailer
Could be the utility company, and ensures that the bills are met by all the consumers. It sends the pricing information to an aggregator.
Aggregators
They collect payment from the consumers and pay the retailer. The HEMS provides the aggregator with load profile and status information. Using this, the aggregator calculates a suitable electricity price and sends it to the HEMS.
Smart Grid/Solar Panels
Supplies electricity.
Smart HEMS
Smart HEMS may have applications installed that display the amount of energy consumed, the consumption prices and status of all the loads and load schedules which can be viewed on various display units such as mobile phones and laptops. Other general information such as weather, seasons, and temperature are also stored and updated daily.
Smart Meter
Records the electricity consumed and sends this data to HEMS and the utility.
Loads
The loads considered in this thesis are cooling systems (such as Air Conditioning), washing machines and EV chargers.
Solar Panel
Used to generate renewable energy and stores this energy into a battery. A controller is used to send status reports about the panel to HEMS.
Battery
The battery stores the energy produced by the solar panel. It provides this same energy to the smart home by discharging during peak hours and charges up through the solar panel. A charge controller provides charge and status information of the battery to the HEMS.
Customers
The HEMS allows the customers living in the smart homes to modify the load schedules and preferences and also provides remote control over the devices. The customers pay directly to the aggregators.
Point 1
The pricing information sent from the retailer to the aggregators can be attacked and manipulated.
Point 2
This same pricing information can be sent to the HEMS system which can again be falsified. The load profile and status information sent back by the HEMS to the aggregators can also be attacked and changed.
Point 3
The status & scheduling information from the solar panels and the battery sent to the HEMS can be attacked too, convincing the HEMS system that the battery is not charged. These attacks may not allow the system to shift to the battery during peak hours, leading to an increase in electric bills.
Point 4
The meter readings from the smart meter to the HEMS can be attacked and the data can be manipulated, leading to wrong calculations of the electricity consumption costs.
Point 5
The performance & scheduling information sent by the loads to the HEMS can be falsified and their energy consumption rates can be falsely increased, leading to an increase in the prices.
Point 6
The hacker can also take control of the system by impersonating the customers. He/she can change the load schedule, preferences and instructions for a short while and send this information to the HEMS.
Process Methodology
Once the attack points were narrowed down, it was time to design a simulation test rig made on MATLAB, and also simulate the schedulable loads, solar panel, grid & battery, and calculate the unit price. After simulating the model, an optimization technique was used to create an optimized (that consumed less energy) HEMS model.

Genetic Algorithm uses the concept of biological evolution on constrained or unconstrained optimization problems to produce an optimized solution. The algorithm randomly selects individuals from a population that has been created by modifying individual solutions (that are grouped together) repeatedly. Based on certain optimizing constraints, the selected individuals are used as parents to produce offspring for a new population. This process is repeated multiple times using sorting & swapping to finally generate an “evolved” or “optimized” solution.
Simulating a cyber-attack on unit pricing
For this test rig, one type of cyber-attack was simulated. This attack targeted the unit price data. The attack was carried out in various ways: (a) Arrange unit price in ascending order (b) in descending order (c) Flip the unit price completely
Testing
Introducing detection techniques
4 detection techniques were used to calculate the difference between the predicted optimized grid & values vs the newly designed attacked grid & values.
.png)
If the predicted unit price and the attacked unit prices were graphed, it is very easy to detect the changes and conclude that an attack has taken place.
Impact
Consequences of the attacks
-
The changes in the cost and energy may lead the loads to shift their schedules to a new time period since these loads will be trying to accommodate the changes into their optimization algorithms.
-
If the attack targets multiple smart homes at the same time, all their appliances may try to schedule during the same time frame, leading to a sudden rise in energy consumption on a whole.
Proposed Solutions
Mitigation techniques
Several mitigation techniques can be used to prevent the attacks from affecting the HEMS and disrupting the cost and energy consumption.

Scheduling Constraints
The HEMS model maintains a stable, user-controlled experience, ensuring that even during attacks, energy usage stays within familiar, scheduled limits.

Generating Alert System
Unexpected outcomes can trigger alerts to both users and aggregators, ensuring transparency and quick action.

Forcing the Algorithm to Follow the Historical Data Pattern
If an attack is detected, the system reverts to familiar historical patterns, maintaining a consistent and trusted user experience.
Insights
Key Takeaways
01
This was a scientific thesis that took me the entire 4th year of my undergrad degree! However, I realized it can be applied in the field of UX as well, since it displays my in-depth research skills.
02
I graduated during COVID, so I never got a chance to display my work in person, and instead presented my paper in an online forum organized by IEEE. I am also very grateful to my mentor and co-author of this paper, Dr Haile Rajamani, who guided me through every step of the way.
03
Publishing this paper in IEEE was a cherry on the top of my degree, but it was not so fun cutting down an extensive 80 page thesis into a 6 page report for publishing!